SECURITY

How does DDoS Protection work?
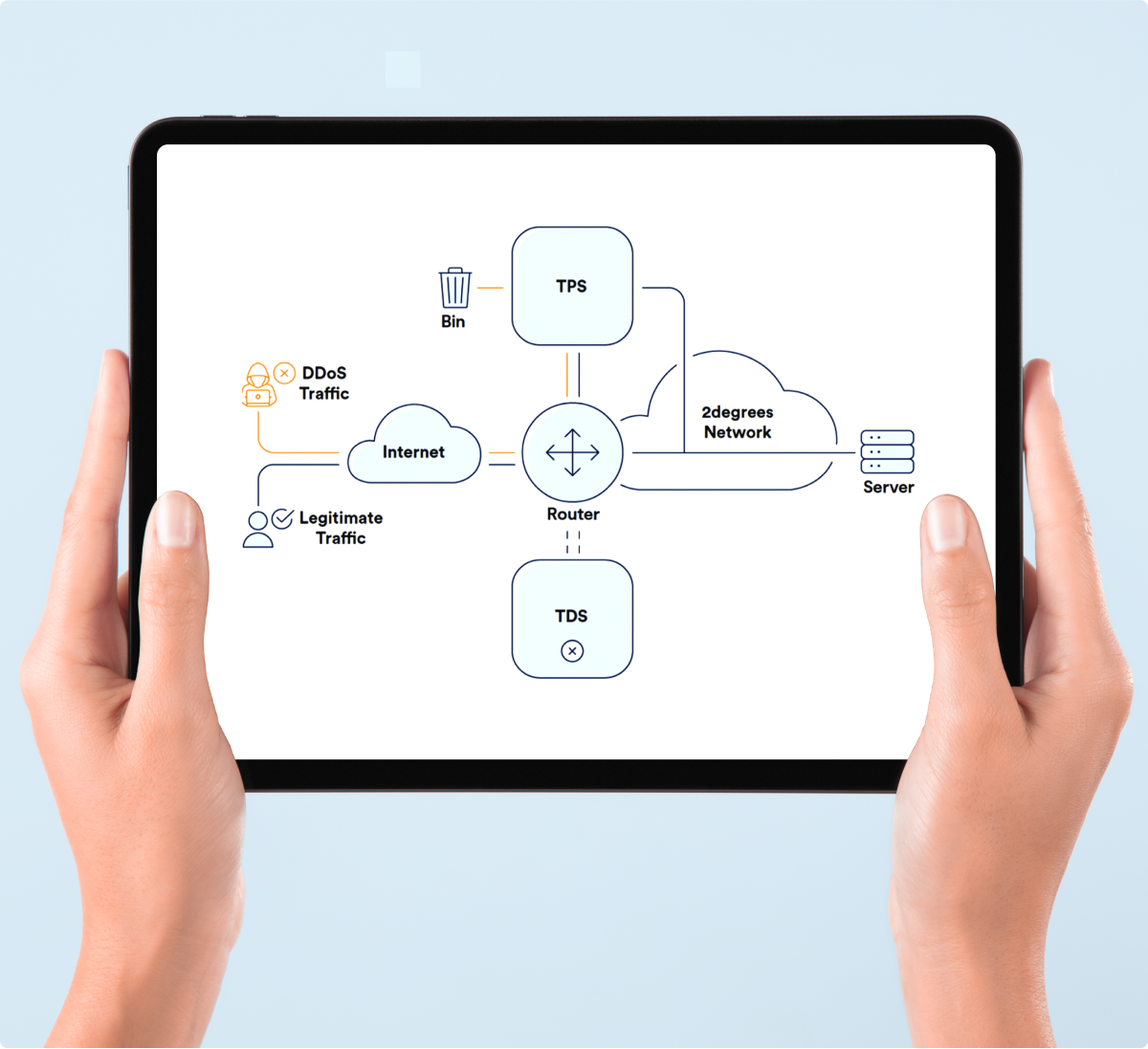
To filter out known attacks before they even reach your network we deliver real-time shields-up DDoS monitoring and mitigation. Our ongoing investment in detection and protection ensures your network is always up and running, even when under attack.
Self-managing DDoS Protection with Flex
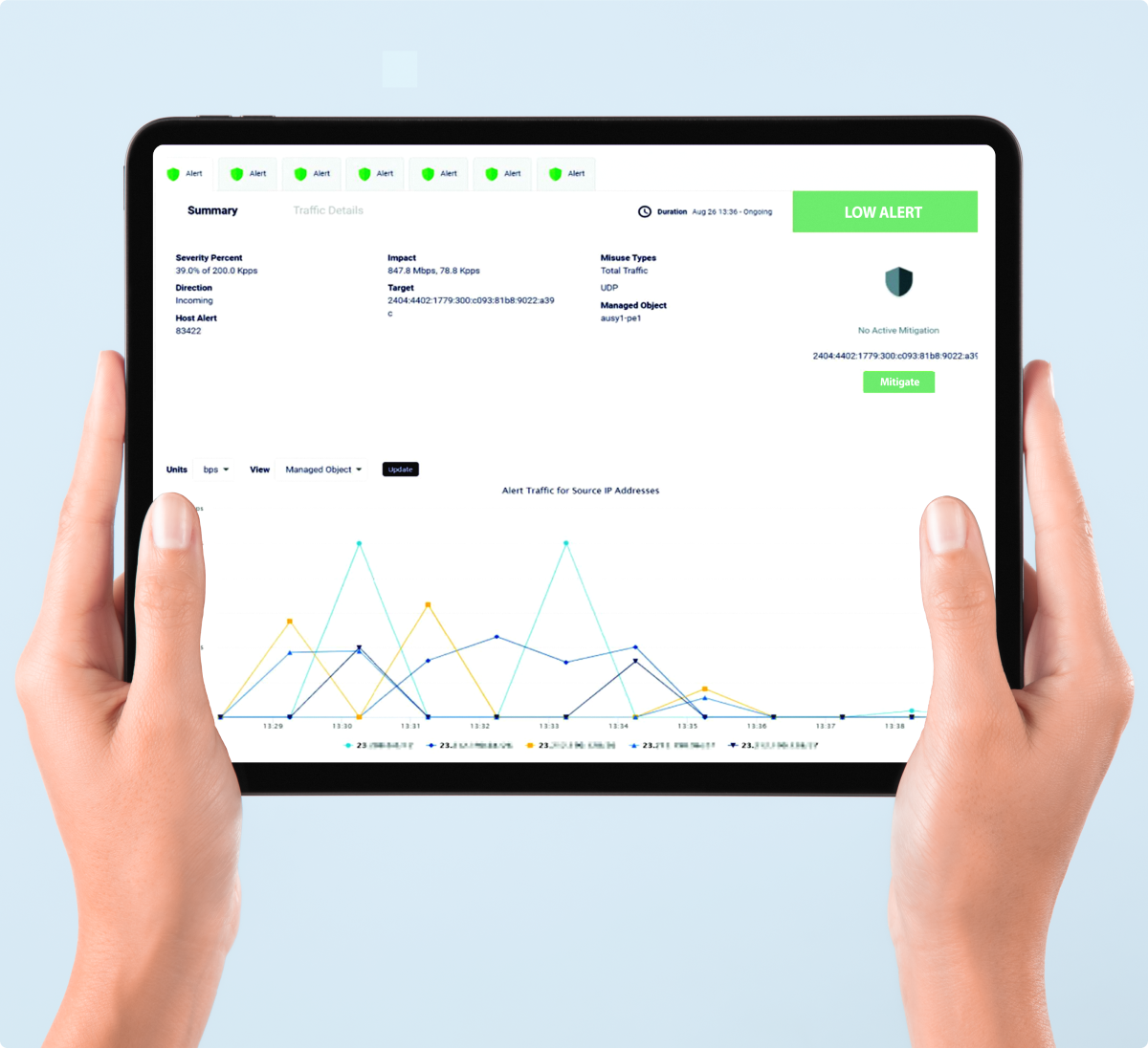
DDoS Protection services can be easily managed via our Flex customer portal. With its intuitive, modern interface, Flex gives approved team members the ability to configure host detection rules to respond and mitigate DDoS attacks in real time in an easy, efficient way.
Core features
Service types
Service breakdown
| Features and benefits | Standard DDoS Protection | Advanced DDoS Detect | Advanced DDoS Protect |
|---|---|---|---|
| Monitoring | |||
| Configurable detection rules | ✕ | ✓ | ✓ |
| Traffic reports to adjust thresholds | ✕ | ✓ | ✓ |
| Automated incident alerts | ✕ | ✓ | ✓ |
| Alert summary and detailed data | ✕ | ✓ | ✓ |
| Real-time attack information | ✕ | ✓ | ✓ |
| Monitoring & reporting for specific IP addresses | ✕ | ✓ | ✓ |
| DDoS event history | ✕ | ✓ | ✓ |
| Mitigation | |||
| Automatic network wide DDoS protection | ✓ | ✓ | ✓ |
| RTBH filtering via BGP | ✓ | ✓ | ✓ |
| RTBH filtering via NOC | ✓ | ✓ | ✓ |
| Manual per incident traffic scrubbing | ✕ | ✓* | ✓ |
| Automatic traffic scrubbing using mitigation rules | ✕ | ✕ | ✓ |
| Service and Support | |||
| NOC Support 24x7 | ✓ | ✓ | ✓ |
| Self-management via Flex customer portal | ✕ | ✓ | ✓ |
*Additional fees apply